Download the PDF version of Problem Set 8 here. Please attempt the questions before coming to class, and be prepared to present your solutions.
Screencast 10
I am sorry that the first 10 minutes of the lecture was not recorded. You did not miss much though.
(This is my 100-th video on Vimeo!)
CS2105 in the News: Global Internet security “keys” generated for the first time at NUS
This project is part of a global effort to make the whole DNS secure and the Internet safer. The DNS is the directory that links web addresses to numerical IP addresses. Without the DNS, people would have to type difficult-to-remember numbers instead of a memorable name to get to a website or send an email.
Using a master key, the keyholders generate cryptographic keys that are used to sign domains, verifying that each entry on the DNS directory is authentic. This prevents a proliferation of fake web addresses which could lead people to malicious sites, which can be used to hack computers or steal credit card details.
Lecture 11: Physical Layer
7 April, 2014.
Finally, we have reached the bottom layer: let’s get physical! We will see how 1s and 0s can encoded into digital and analog signals for transmissions.
Slides: PDF
Assignment 3
Here’s your Assignment 3 on understanding packet traces.
This is an INDIVIDUAL assignment, due 18 April 2014, 6:00pm.
Please write your answers in the answer sheet and submit a hardcopy to Wei Tsang before the deadline.
(Please ignore the Assignment 3 posted in IVLE — we were struggling to get online assignment working in IVLE, resulting in delay releasing the assignment.)
Assignment 1: Comments
The grades for Assignment 1 has been posted in your IVLE gradebook. Please take a look at the comments, and report back to us if there is anything surprising.
Some of the common mistakes are:
- Returning incorrect HTTP response headers. Some of you return 200 OK, even if the request is incorrect (e.g., requesting for a non-existing file). Some of you return two HTTP status codes, or no HTTP status code, or two lines of content-type. Some of you return content-length with incorrect number of bytes. Despite being the easiest part of the assignment to get right (just following the format!), your submission is surprisingly buggy in this aspect.
- Strong assumption about HTTP request headers. The HTTP request header format does not dictate the order of the fields, except that the first line must be the request line (with method, resource, and version). You cannot assume content-type and content-length appears in a certain order, nor can you assume that the last line in the header is of certain fields.
- For a POST request, you should not assume that the body contains “——WebKitFormBoundary”. In fact, you need not know about the format of the POST body at all, as indicated in the assignment description.
- Some of you did not follow the instructions, which require that you take in the port number as a command line argument. Those who hardcoded the port number loose one point needlessly for not following instructions.
Lecture 10: LAN
30 March, 2014.
This week we will take a look at another multiple access protocol, CSMA/CA for WiFi, and discuss the roles of hubs, switch, and routers in forming a LAN. ARP will be discussed as well.
Slides: PDF
Please read the following sections in the textbook.
- 5.4 Switched Local Area Network (exclude 5.4.4)
- 6.3.1 The 802.11 Architecture
- 6.3.2 The 802.11 MAC Protocol
Problem Set 7
Download the PDF version of Problem Set 7 here. Please attempt the questions before coming to class, and be prepared to present your solutions.
Assignment 2: Test Your Code
I hope everyone is having fun writing your own reliable file transfer program in Assignment 2.
I am releasing the code we will use to test your program. You can use it to check if your code will survive our test cases.
To run the test, execute
~sadm/a2/check.sh <port>
on cs2105-z.comp.nus.edu.sg (replace <port> with your favourite port number).
Note that, passing the test cases just means that your code behaves correctly when tested, it does not mean that your code is correct.
The test script is experimental, so please report if it fails to run.
Screencast 9
Lecture 9: Link Layer
24 March, 2014.
“These Protocols Transmit At Random Interval. It May Sound Ridiculous, But The Reason They Do It Is Simply Beautiful.”
This week we continue our venture down the protocol stack, and look at the link layer. We will review the services provided by the link layer, how error detection/correction is done, how shared medium are accessed, and finish up with a discussion on Ethernet frame format.
Slides: PDF
Please read the following sections in the textbook. Reading: Chapter 5
- 5.1 Introduction to the Link Layer
- 5.2 Error-Detection and -Correction Techniques
- 5.3 Multiple Access Links and Protocols (skip efficiency analysis in 5.3.2)
- 5.4.2 Ethernet – Ethernet Frame Structure (page 497 – 499)
Screencast 8
Problem Set 6
We will start the discussion of Problem Set 6 next week. Download the PDF version of Problem Set 6 here. Please attempt the questions before coming to class, and be prepared to present your solutions.
Midterm Result Released
1. Here is the distribution of your midterm marks. The maximum marks given is 30 (out of 31). The average is 16. Note that the make-up midterm marks are not yet integrated (that explains the seven 0s).
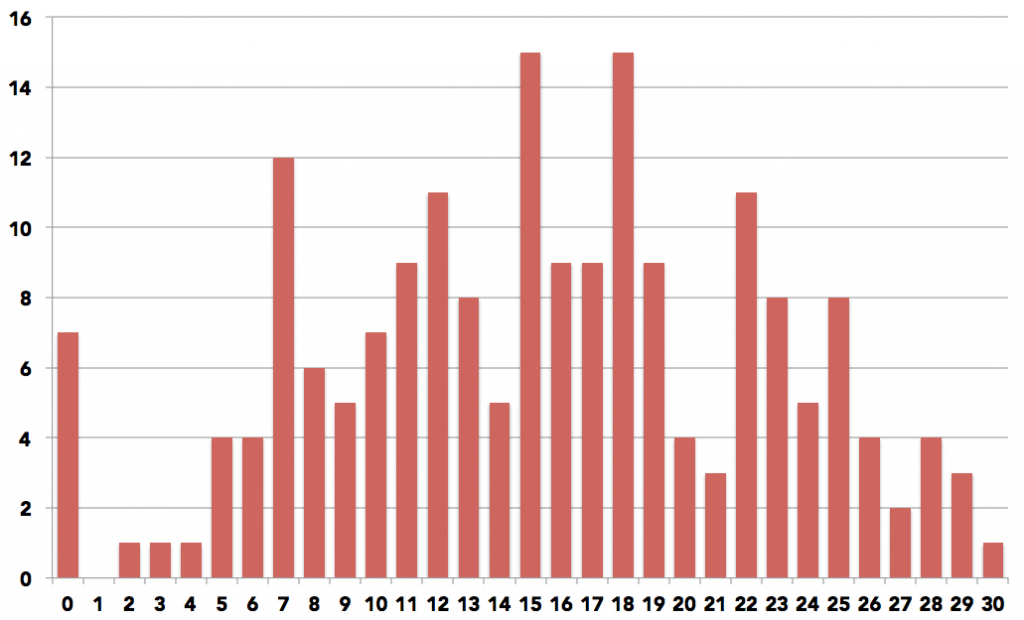
2. You should be getting back your answer sheet this week during your tutorial. Please note the following regarding regrades.
- Please check carefully to make sure there is no error in grading (including summing error and mark entering error)
- Students receiving back the answer sheets this week has until the end of the week to submit the regrade request.
- Please submit the regrade request to the TA, Mr. Saeid, during his office hours, or slip it under my office door with an accompanying note explaining your request.
- Students who receive back the answer sheet after this week can only submit the regrade request “on-the-spot.”
- Please take a look at the marking scheme to understand how we allocate marks, before you request for a regrade.
3. Your midterm mark has been imported into your IVLE gradebook for CS2105.
4. IMPORTANT notes on Q5. We accept both A and C as correct answers. Due to my negligence, C is not marked as the correct answer. You, however, need not submit your answer sheet for regrade if you answered C for Q5 but did not receive 2 marks for that. An additional 2 marks will be added to your midterm grade “digitally”. In other words, you should see that your grade in the gradebook is 2 marks higher than what is noted on your answer sheet. Please inform me if your answer for Q5 is C but you did not receive an additional 2 marks.
Assignment 2
Here’s your Assignment 2 on simulating alternating-bit protocol. This is a simple assignment (the solution is only ~40 lines of code) to be completed and submitted INDIVIDUALLY before 30 March, 2014, 11:59PM. Despite the simplicity, please start early!